Article, Publication
Future developments in standardisation of cyber risk in the Internet of Things
by Dr Petar Radanliev
The PETRAS-RETCON Project has produced a journal paper to examine how cyber risk assessment approaches have been used for the risk assessment of Internet of Things (IoT) devices and networks. The study makes recommendations for adapting current cyber risk assessment principles for measuring the impact from different IoT cyber risk systems.
The RETCON paper:
- Empowers communications network providers to create clear, rigorous, industry-accepted mechanisms to measure, control, analyse, distribute and manage critical data needed to develop, deploy and operate cost-effective cyber security for critical infrastructure
- Provides a documented process representing a new design for mapping and optimising IoT cybersecurity
- Is the first attempt to define the standardisation process for cyber risk impact assessment of IoT vectors
- Offers new design principles for assessing cyber risk
- Proposes a process for adapting existing cybersecurity practices and standards to include IoT cyber risk
- Advances the efforts of integrating standards and governance on IoT cyber risk and offers a better understanding of a holistic impact assessment approach for cyber risk
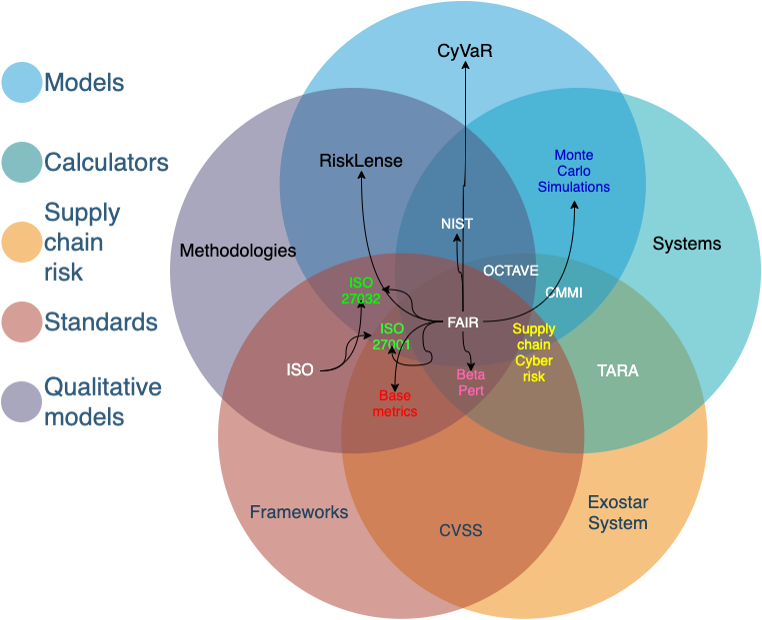
There are various approaches for cyber risk assessment that can be categorised into standards, frameworks, methods, models and even calculators. The complexity of using multiple approaches for risk assessing individual elements of cyber risk in an individual organisation, might seem a bit unnecessary to everyone except the cybersecurity experts.
These approaches are however specifically designed for risk assessing individual risks and are used by cybersecurity professionals as tools, very much in the same way a plumber would use different tools for checking the pipes of an old house.
Take for example the most famous approach – the National Institute of Standards and technology (NIST). As described in the title, NIST is a standard and provides a framework that already integrates various existing standards, guidelines, and practices to simplify the process and enable organisations to manage and reduce cyber risk.
The main take on NIST is that it’s a qualitative approach, describing a path for organisations to take, depending on their risk appetite, requirements, objectives, and most importantly their resources. NIST tells you what to do, to reach a certain level of cybersecurity, but it fails short of providing a method to quantitatively measure the financial loss from cyber risks specific to your organisation. NIST is a qualitative framework, very much the same as the International Organisation for Standardisation (ISO) and the International Electrotechnical Commission (IEC) – these are all standards.
The Factor Analysis of Information Risk (FAIR) institute is on the other hand a framework that contains a quantitative model for risk assessment of information security and operational risk. The FAIR model is specifically designed to complement all qualitative standards and provides organisations with a tool for calculating the financial risk and the potential loss scenarios. In other words, with the FAIR model, you can place a dollar value on risk, and you won’t be able to do that with NIST, ISO or IEC. The long list of cyber risk assessment standards, frameworks, methods, models and calculators is described in the technical paper, including examples of each approach.
Until recently, these approaches made very little provisions on how to assess the emerging risks from IoT systems. This has started to change and NIST has already published a program [PDF] for IoT cybersecurity . Nevertheless, many other approaches are not catching up with the new and emerging risks from IoT systems. This adoption of IoT risk in the cyber risk assessment needs to happen at much faster pace. Because IoT devices are getting connected at a fast and growing rate, increasing the cyber-attack surface, while new risks remain undetected by organisations that are compliant with existing risk assessment standards. Even without the IoT risk, the increasing complexity of various different approaches, was creating some confusion among practitioners and occasionally even with cybersecurity experts.
A standardised approach for clarifying the complexity of various and diverse approaches, that integrates the IoT risk, is presented in the full text of the technical paper. The technical paper presents a framework for standardisation of cyber risk assessment. With a focus on understanding IoT cyber risk in national high-tech strategies, presenting examples from across the globe – including the UK Digital Strategy. The lack of standardised approach in the past, for risk assessing these systems, meant that many IoT systems were installed and unreported to the security professionals, which often resulted with cyber risk from IoT systems being undetected by cybersecurity professionals. The new framework categorises and classifies the IoT cyber risk systems into ‘vectors’ and describes how we can modify current cyber risk assessment approaches to integrate the cyber risk from IoT systems.
Key publication:
Radanliev, Petar., De Roure, David., Nurse, Jason R. C., Mantilla Montalvo, Rafael., Cannady, Stacy., Santos, Omar., Maddox, La’Treall., … Maple, Carsten, “Future developments in standardisation of cyber risk in the Internet of Things (IoT),” SN Appl. Sci., vol. 2, no. 2, pp. 1–16, Feb. 2020. (Open Access) – Link: https://doi.org/10.1007/s42452-019-1931-0